Decrypting D-Link XOR Encrypted Firmware
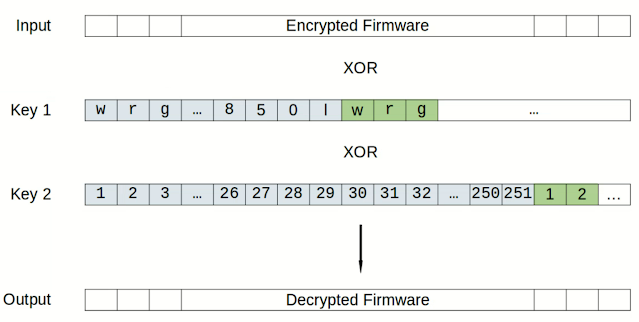
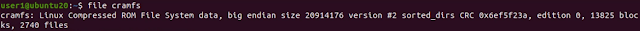
Firmware DIR850LB1_FW207WWb05.bin is encrypted with XOR cipher. Original firmware is XORed with two keys. First key is wrgac25_dlink.2013gui_dir850l Second key is numbers from 1 to 251. Python program to decrypt the firmware is given below: import itertools import sys key1 = itertools.cycle(b'wrgac25_dlink.2013gui_dir850l') key2 = itertools.cycle(range(1, 252)) with open(sys.argv[1], 'rb') as f: fw = f.read() with open(sys.argv[2], 'wb') as f: for i in range(0, len(fw)): f.write(bytes([fw[i] ^ next(key1) ^ next(key2)])) Demo