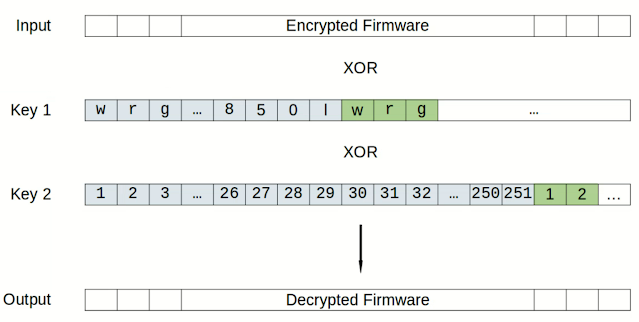
Decrypt TP-Link config.bin Configuration Backup File

Configuration backup file can be downloaded from certain TP-Link devices by clicking Backup button on System Tools > Backup & Restore page. The downloaded configuration file, config.bin is encrypted. To decrypt the config.bin file, use key 478DA50BF9E3D2CF. openssl enc -d -des-ecb -nopad -K 478DA50BF9E3D2CF -in config.bin -out dec_config.bin First 16 bytes of the output file, dec_config.bin is the MD5 hash of configuration text file. Decrypted file may also contain null byte padding at the end. In this case there are 4 null bytes at the end of file. To extract configuration text file, remove MD5 hash (First 16 bytes) and padding (Last 4 bytes). dd if=dec_config.bin of=config.txt bs=1 skip=16 truncate -s -4 config.txt Output file, config.txt contains the configurations. Its MD5 hash should match the MD5 given in dec_config.bin. Demo